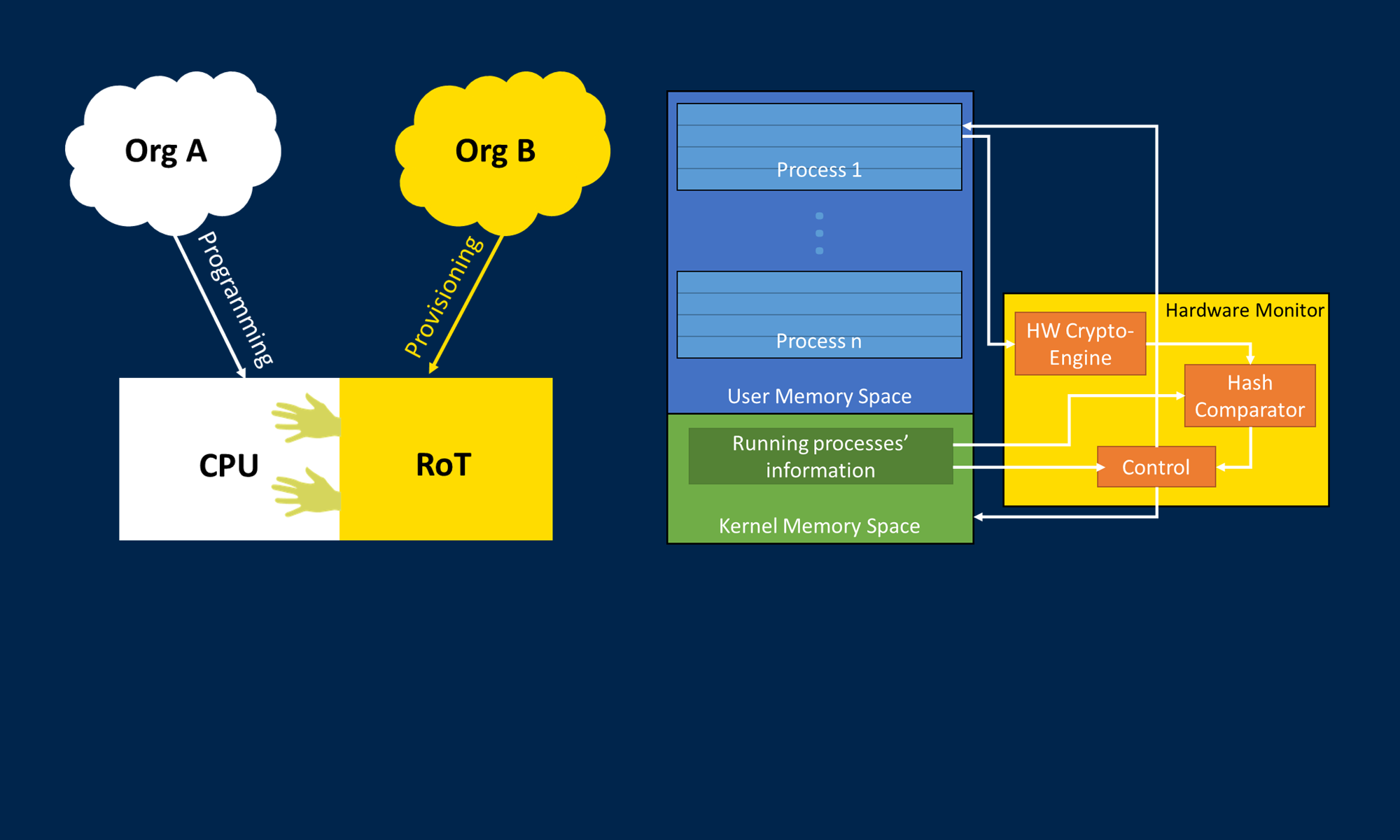
GridTrust Native Device Setup
The GridTrust Native Device is an industrial temperature sensor. Representative updates (in the form of text files) for the device include changing the format for reporting temperatures.
The native device is connected to the computer via USB. The connection to the computer is USB-A, whereas the connection to the native device is USB-B.
The native device setup communicates with the server (via a networking switch, connected to the laptop with ethernet).
The PUF board is connected to the computer via USB. The connection to the computer is USB-A, whereas the connection to the PUF board is USB-C.
Source Code
Devices Utilized
The Device demo is comprised of multiple COTS components:
-
- Arduino Uno
- LM95172 Temperature Sensor
- NXP LPCXpresso55S69 (PUF)
- Dell Optiplex 7000
Setup
The Dell computer interfaces with the GridTrust Server and maintains communications with the PUF board and the Arduino. The Arduino in turn performs serial communications with the temperature sensor.
- Install Rust
- Install OpenSSL
- sudo dnf -y install openssl openssl-devel
- Create a new Rust project
- cargo new native
- Replace files in /client/code/src with Github native/code/src files
- Replace /client/code/Cargo.toml with Github native/code/Cargo.toml
- cargo build
- The native device file structure is relative to the Rust project root directory (the directory containing Cargo.toml):
- ./local_updates/ directory
- ./local_updates/util_sign64.txt is the utility signature in base 64 format (from server setup)
- ./local_updates/vendor_sign64.txt is the vendor signature in base 64 format (from server setup)
- ./local_updates/update64.txt is the update file in base 64 format
- ./updater/ directory
- ./updater/utility.pub.pem is the utility public key file generated during the server setup
- ./updater/vendor.pub.pem is the vendor public key file generated during the server setup
- ./updater/gridtrust.pfx is the .pfx file generated during the server setup
- ./updater/ca2.crt is the .crt file generated during the server setup, the same certificate file Nginx uses. During the server setup, it was generated as ca.crt, but can be renamed to ca2.crt
- ./base64.sh is the shell script called by the Rust code during the decoding and verification of intermediate signature and update files
- ./local_updates/ directory
- Configure the native device computer to trust the server certificate:
- Copy ./updater/ca2.crt to /etc/pki/ca-trust/source/anchors/ca2.crt
- Run the command sudo update-ca-trust
- Ensure that base64.sh is executable: chmod +x base64.sh
If a native device is configured with incorrect signatures or certificates, then authentication will fail.