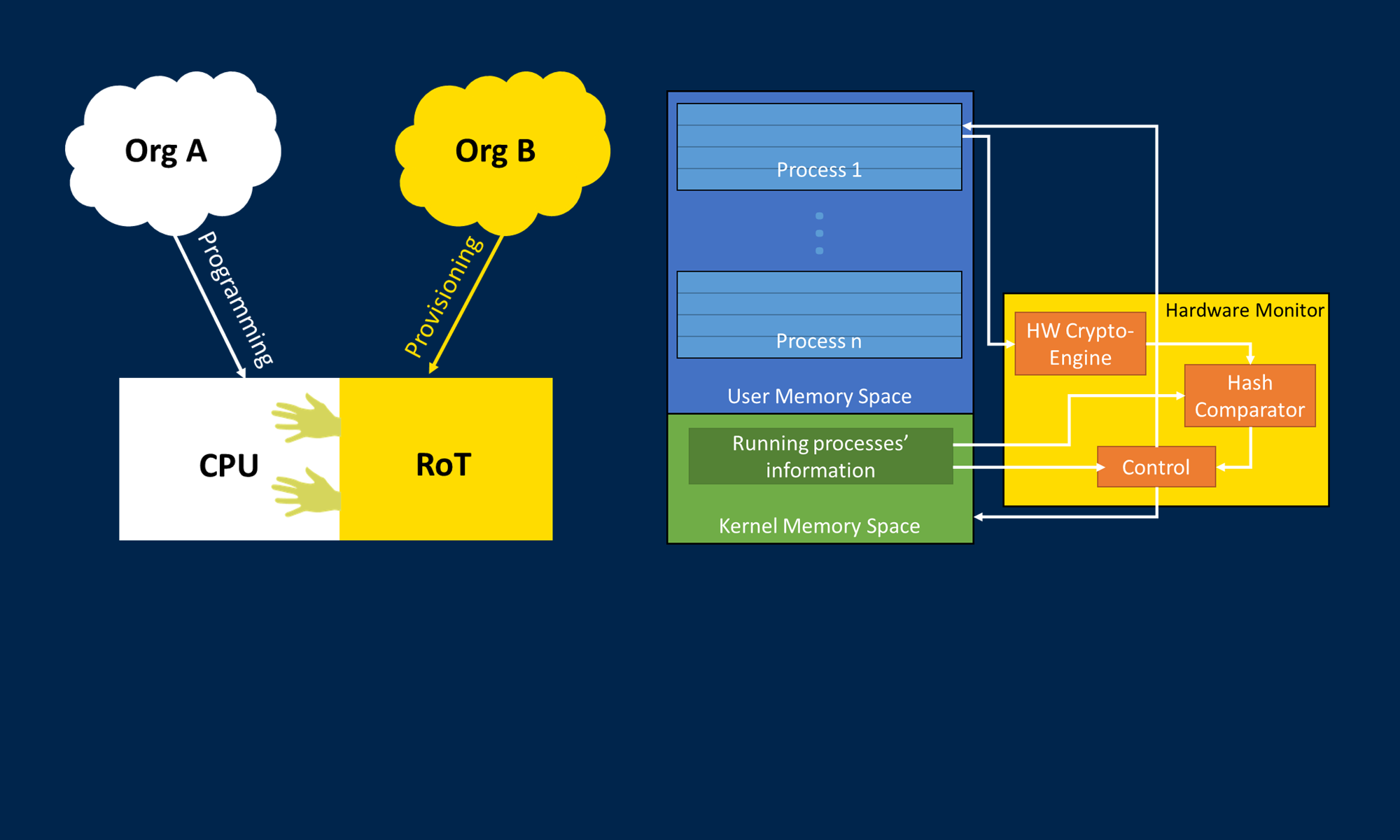
Hardware/software co-designed systems are increasingly prevalent due to trends such as the adoption of hardware accelerators and the availability of heterogeneous system-on-chip (SoC) architectures. A potential security concern arising from hardware/software interaction in heterogeneous computing architectures is the possibility of software-based attacks on reconfigurable hardware, and vice versa. This is especially important when considering remote updates of the software, hardware, or both combined. In this work, we propose a remote update scheme that relies on a hardware root-of-trust and multiple updating parties to deliver hardware/software updates in a secure fashion. The root-of-trust secures all cryptographic computations, as well as remote authentication, key storage, and update image integrity verification. By moving these operations down to a root-of-trust, the attack surface is limited such that, in the event of an attack from outside the root-of-trust (either from software or reconfigurable hardware), all security-critical computations and data remain inaccessible to the attacker. Furthermore, the proposed scheme aims to provide a high level of assurance that the system only accepts updates from approved entities while also preventing common remote attacks from compromising the security of the update process.
Collaborators
Publications
K. Hutto, S. Paul, B. Newberg, V. Boyapati, Y. Vunnam, S. Grijalva, V. Mooney, “PUF-Based Two-Factor Authentication Protocol for Securing the Power Grid Against Insider Threat,” Kansas Power and Energy Conference (KPEC’22), April 2022.
B. Newberg, S. Grijalva, V. Mooney, “Open-Source Architecture for Multi-Party Update
Verification for Data Acquisition Devices,” Power and Energy Conference at Illinois, March 2022.