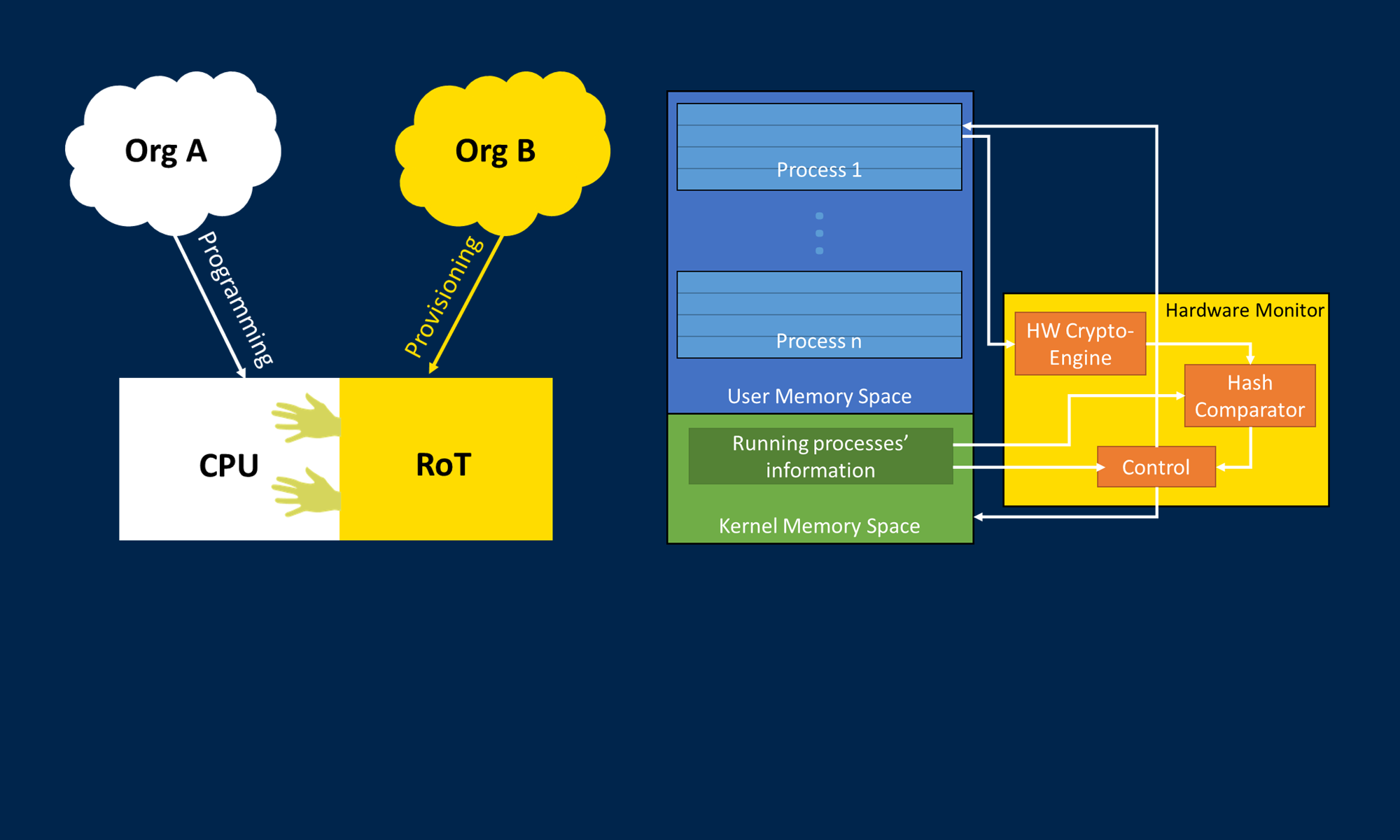
An embedded device in an insecure environment is subject to additional security risk through capture and reverse-engineering by a capable adversary. If this device contains a microchip performing sensitive computations, capture of the chip may leak functionality to an adversary. We propose a novel method in which we randomly encode the input operands and the outputs of a computation, thus not revealing the arithmetic operations being performed. The operations are sequenced in a graph representing the overall application. Once the initialization values are overwritten and lost, the results of these computations are indecipherable by the device performing the calculations as well as by any adversary. The result is transmitted back to a secure server which has stored the initialization values and so can decode the results which appear random to the adversary.
Publications
Kevin Hutto, Santiago Grijalva, and Vincent Mooney. 2022. Hardware-Based Randomized Encoding for Sensor Authentication in Power Grid SCADA Systems. In 2022 IEEE Texas Power and Energy Conference (TPEC). 1–6. https: //doi.org/10.1109/TPEC54980.2022.9750706
Kevin Hutto, Santiago Grijalva, and Vincent Mooney. 2022. RanCompute: Computational Security in Embedded Devices via Random Input and Output Encodings. In 2022 11th Mediterranean Conference on Embedded Computing (MECO). 1–8. https://doi.org/10.1109/MECO55406.2022.979715022
Kevin Hutto and Vincent Mooney. 2021. Sensing with Random Encoding for Enhanced Security in Embedded Systems. In 2021 10th Mediterranean Conference on Embedded Computing (MECO). 1–6. https://doi.org/10.1109/MECO52532.2021.9460190