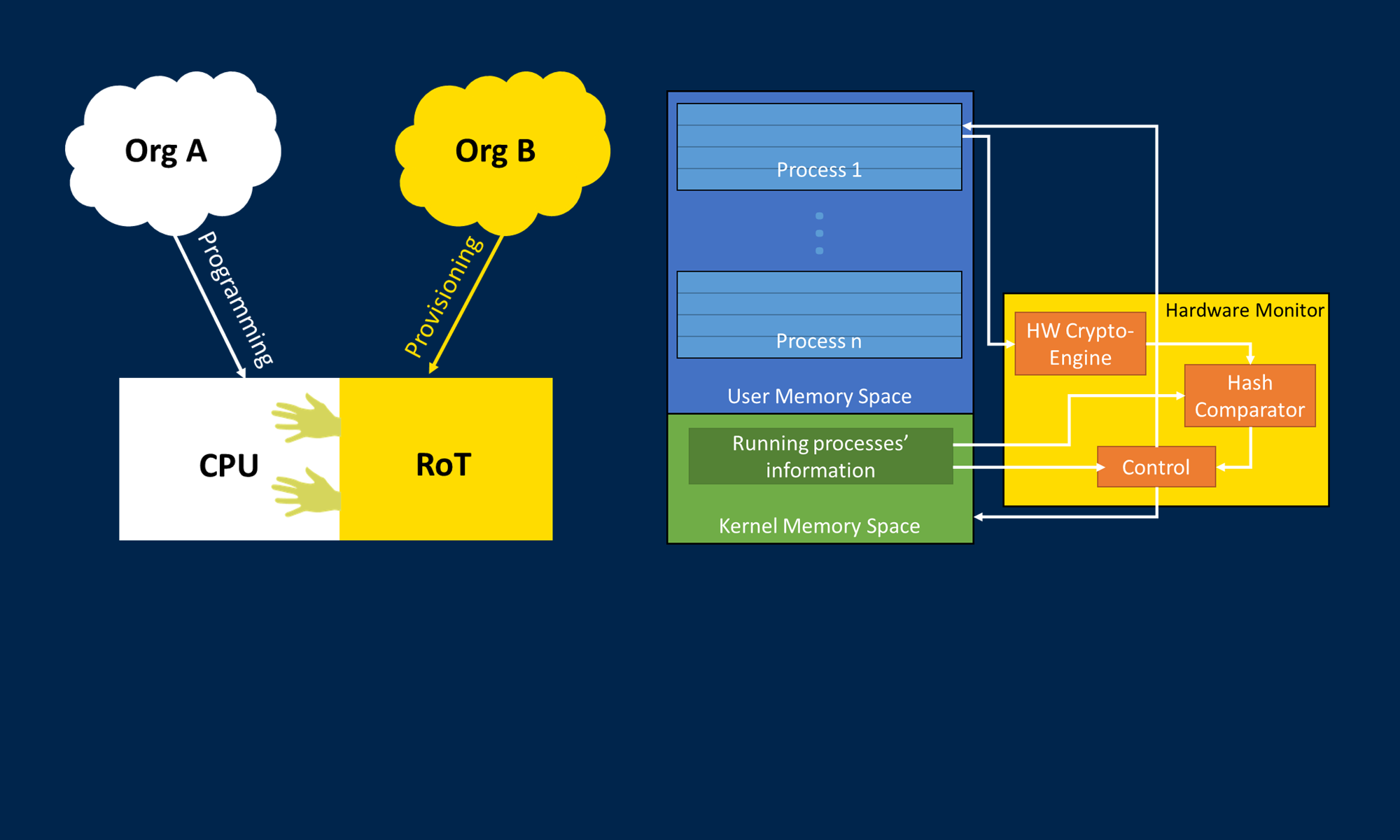
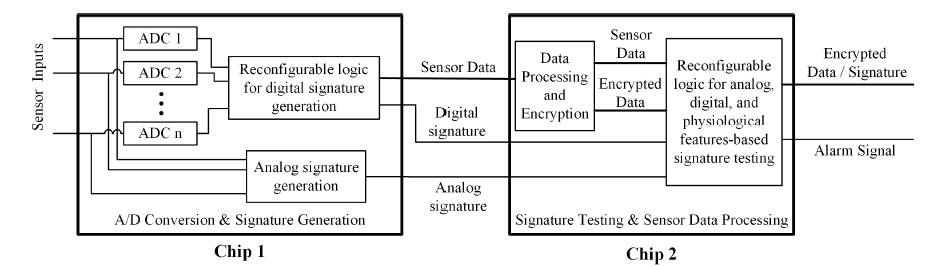
Recent chip manufacturing technology provides billions of transistors at device sizes so small that hardware alterations in the fabrication process cannot be detected if small enough (e.g., a few gates). As such, hardware attacks may pass traditional digital systems test (e.g., built-in self test) yet corrupt critical functionality resulting in dramatic harm. This nascent research project aims to invent an approach based on hardware signatures where malicious hardware alterations to chip functionality are detected prior to any negative impact on the system. For example, a signature can be added in the analog to digital conversion of a sensor’s inputs and passed on to the analysis, processing and encryption chip; the signature can thus be checked to detect any nefarious alterations to functionality, including hardware attacks on input bits.
Corruption of data in embedded and medical devices can cause serious harm if not quickly detected. Our research emphasizes the part of the attack surface which entails inserting malicious hardware circuitry (Hardware Trojans) during the manufacturing process of a digital microchip. A Hardware Trojan (HT) is composed of a few gates and attempts to modify the functionality of the chip. In this work, we present an architecture that involves splitting the design into a two-chip approach, generating signatures deep in the hardware during data harvesting, and then checking for these signatures during data processing and encryption for transmission. In addition, we take advantage of known physiological relationships between medical data to ensure the integrity of the data that is processed by the hardware.
Faculty
Publications
- T. Wehbe, V. Mooney, D. Keezer, O. Inan and A. Javaid “Use of Analog Signatures for Hardware Trojan Detection,” Proceedings of the 14th FPGAworld Conference (FPGAworld’17), ACM, Sept. 2017, pp. 15-22.
- T. Wehbe, V. Mooney, A. Javaid and O. Inan “A Novel Physiological Features-Assisted Architecture for Rapidly Distinguishing Health Problems from Hardware Trojan Attacks and Errors in Medical Devices,” IEEE International Symposium on Hardware Oriented Security and Trust (HOST’17), May 2017, pp. 106-109.
- T. Wehbe, V. Mooney, D. Keezer and N. Parham “A Novel Approach to Detect Hardware Trojan Attacks on Primary Data Inputs,” Proceedings of the 2015 ACM Workshop on Embedded Systems Security (WESS’15), Article 2, 10 pages, October 2015. Presentation (pdf)
- A. Gbade-Alabi, D. Keezer, V. Mooney, A. Poshmann, M. Stöttinger and K. Divekar “A Signature Based Architecture for Trojan Detection,” Proceedings of the 2014 ACM Workshop on Embedded Systems Security (WESS’14), October 2014. Presentation (pdf)